Three papers from VCG Members accepted at ICCV 2021
Papers on supervised video person re-identification and adversarial attacks accepted at ICCV 2021-
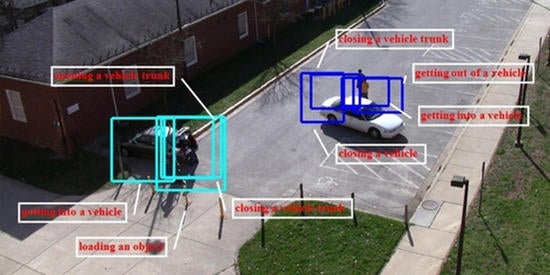
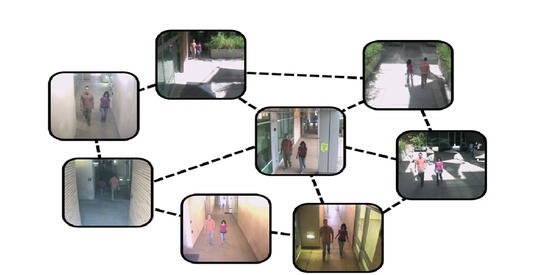
The paper titled "Spatio-Temporal Representation Factorization for Video-based Person Re-Identification" proposed a flexible new computational unit, Spatio-Temporal Representation Factorization module (STRF), that can be used in conjunction with most existing 3D convolutional neural network architectures for re-ID. The key innovations of STRF over prior works include explicit pathways for learning discriminative temporal and spatial features to capture complementary person-specific appearance and motion information.
Title: Spatio-Temporal Representation Factorization for Video-based Person Re-Identification.
A. Aich, M. Zheng, S. Karanam, T. Chen, A. Roy-Chowdhury, Z. Wu, International Conference on Computer Vision (ICCV), 2021. -
The paper titled "Multi-Expert Adversarial Attack Detection in Person Re-identification Using Context Inconsistency" proposed the first adversarial attack detection strategy, i.e. multi-expert adversarial attacks detection (MEAAD), for the defense of person re-ID systems. Specifically, three kinds of context inconsistencies caused by adversarial attacks are employed to learn a detector for distinguishing the perturbed examples.
Title: Multi-Expert Adversarial Attack Detection in Person Re-identification Using Context Inconsistency.
X. Wang, S. Li, M. Liu, Y. Wang, A. Roy-Chowdhury, International Conference on Computer Vision (ICCV), 2021. -
Motivated by the observation that language descriptions of natural scene images have already captured the object co-occurrence relationships that can be learned by a language model, the paper "Exploiting Multi-Object Relationships for Detecting Adversarial Attacks in Complex Scenes" developed a novel approach to perform context consistency checks using language models. The distinguishing aspect of this approach is that it is independent of the deployed object detector and yet offers very high accuracy in terms of detecting such examples in practical scenes with multiple objects.
Title: Exploiting Multi-Object Relationships for Detecting Adversarial Attacks in Complex Scenes.
M. Yin, S. Li, Z. Cai, C. Song, S. Asif, A. Roy-Chowdhury, S. Krishnamurthy, International Conference on Computer Vision (ICCV), 2021.